Cloud Productivity Migration
Move CRM, accounting, HR, and file platforms with full data integrity and user confidence.

Battle-tested playbooks and validated checklists for every workload.

Least-privilege access, encrypted transport, and audit trails for every change.

Validation at every stage with rollback plans and recovery checkpoints.

Solution architects, project managers, and cutover engineers aligned to your team.




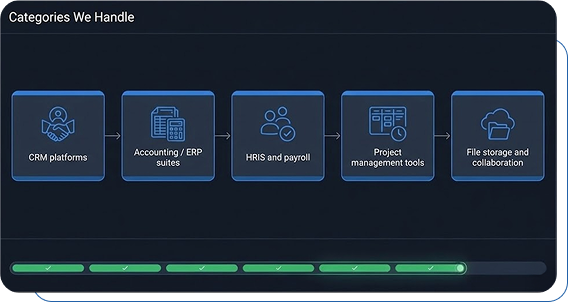

Objects, pipelines, activities, and attachments validated.

Custom fields, roles, and workflow alignment.

Ledgers, customers, vendors, and transactions balanced.

Subsidiaries, items, and historical transactions reconciled.

Permissions, sharing links, and metadata preserved.
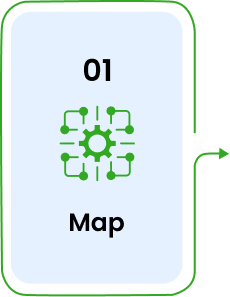
Define source and target data structures.
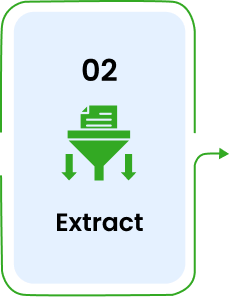
Gather data from source systems.
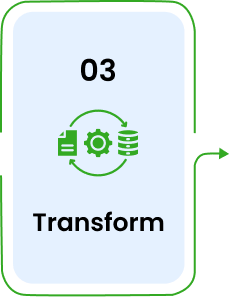
Cleans and format data for target.
Ensure data quality and accuracy.
Import data into the new system

UAT acceptance testing and approval.